Chapter 11: AWS KMS and AWS CloudHSM
.-.. --- -.-. -.- / ..- .--. / -.-- --- ..- .-. / -.- . -.-- ... / -... ..- - / -.. --- -. .----. - / - .... .-. --- .-- / .- .-- .- -.-- / - .... . / -.- . -.--
Was does it say? You need the key (click here to hear it)
There are two types of code systems, symmetrical key and asymmetrical key.
The symmetrical key system requires the encoding and decoding of a message to be done using the same key. So both sender and receiver need to have a copy of the identical key. The weakness with this approach is that you have to transmit the key somehow in the 1st place (or have a shared secret such as using a book as the source of keys). This sort of cryptosystem has been used for ages.
The German Enigma system was a symmetric key system:
Enigma featured the major operational convenience of being symmetrical (or self-inverse). This meant that decipherment worked in the same way as encipherment, so that when the ciphertext was typed in, the sequence of lamps that lit yielded the plaintext.
Identical setting of the machines at the transmitting and receiving ends was achieved by key setting procedures. These varied from time to time and across different networks. They consisted of setting sheets in a codebook.[21][22] which were distributed to all users of a network, and were changed regularly. The message key was transmitted in an indicator[23] as part of the message preamble. The word key was also used at Bletchley Park to describe the network that used the same Enigma setting sheets. Initially these were recorded using coloured pencils and were given the names red, light blue etc., and later the names of birds such as kestrel.[24] During World War II the settings for most networks lasted for 24 hours, although towards the end of the war, some were changed more frequently.[25] The sheets had columns specifying, for each day of the month, the rotors to be used and their positions, the ring positions and the plugboard connections. For security, the dates were in reverse chronological order down the page, so that each row could be cut off and destroyed when it was finished with.[26]
The British managed to break the naval enigma first (I think because they had recreated the naval enigma machine and also had some captured code books? This is the problem with symmetrical codes, if you loose the code anyone can read your message) An enigma machine:
If you know that the above code is Morse and know Morse you can read it. The Morse code above said: "Lock up your keys but don't throw away the key". Funny, Morse was invented as the 1st code to communicate with across wires, and it was BINARY!
Asymmetric crypto systems are like a party trick. Every time I hear the explanation of how they work I think oh that's obvious and then immediately forgot it. They weren't invented until just before I was a few years old (in computer science terms) in the late 1970's. Also called public/private key crypto, RSA and PGP are some early versions. They were considered as research curiosities in the early 80's. There are 2 keys which are always paired. The public key is well, public. It is used to encode a message which is sent to someone who has the matching private key. They can then decode the message and determine if it was from the holder of the public key. I.e. it works for authentication (ensure that the message is from who you think it's from) and encryption (preventing anyone else reading the message or changing it). The private key is generated by computer from the public key, but it's a complex computational operation that is theoretically unsolvable in a useful period of time. It's also more computationally demanding than symmetrical crypto so tends to be used for short messages, digital signatures, or to encrypt the symmetrical keys which are then used for larger messages.
Wikipedia explains the two crpto systems in terms of how you can use the public postal system to send messages, someone needs to draw a picture of this:
An analogy that can be used to understand the advantages of an asymmetric system is to imagine two people, Alice and Bob, who are sending a secret message through the public mail. In this example, Alice wants to send a secret message to Bob, and expects a secret reply from Bob.
With a symmetric key system, Alice first puts the secret message in a box, and locks the box using a padlock to which she has a key. She then sends the box to Bob through regular mail. When Bob receives the box, he uses an identical copy of Alice's key (which he has somehow obtained previously, maybe by a face-to-face meeting) to open the box, and reads the message. Bob can then use the same padlock to send his secret reply.
In an asymmetric key system, Bob and Alice have separate padlocks. First, Alice asks Bob to send his open padlock to her through regular mail, keeping his key to himself. When Alice receives it she uses it to lock a box containing her message, and sends the locked box to Bob. Bob can then unlock the box with his key and read the message from Alice. To reply, Bob must similarly get Alice's open padlock to lock the box before sending it back to her.
The critical advantage in an asymmetric key system is that Bob and Alice never need to send a copy of their keys to each other. This prevents a third party – perhaps, in this example, a corrupt postal worker who opens unlocked boxes – from copying a key while it is in transit, allowing the third party to spy on all future messages sent between Alice and Bob. So, in the public key scenario, Alice and Bob need not trust the postal service as much. In addition, if Bob were careless and allowed someone else to copy his key, Alice's messages to Bob would be compromised, but Alice's messages to other people would remain secret, since the other people would be providing different padlocks for Alice to use.
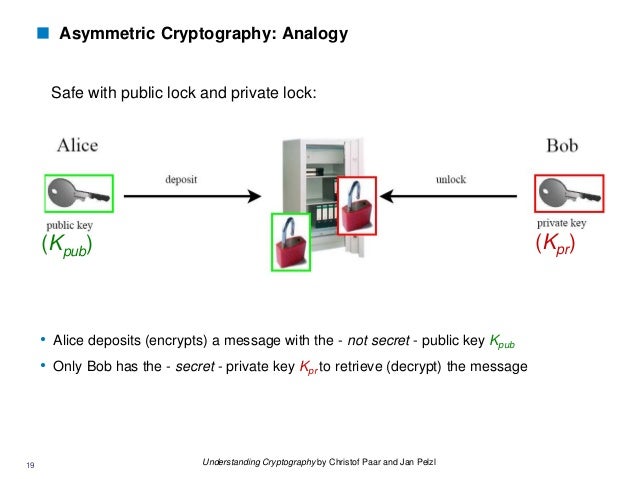
A picture using the keybox analogy:
A complete system involves a few more components, including certification authorities (who can issues keys and keep them), and revocation of keys (timebound, or on demand).
For a period it was dangerous to have and communicate the RSA algorithm outside the USA, it was classed as a banned munition (similar to the PS2 they were worried it could be used for missile guidance systems).
http://www.cypherspace.org/adam/shirt/
Oh and of course the code is in code (ha ha).
Looking for a crypto cartoon I found this. A stick figure guide to advanced encryption (some people have too much time on their hands!?)
Is there something encoded in the cartoons I wonder?
And a cartoon.
So back to the plot, what does AWS KMS and AWS CloudHSM do?
KMS is a key management service. The crypto details are here (not stick figures :-( )
According to the book it's only for symmetric key management (generation, store, enable/disable, delete). The keys always stay inside AWS so you can't lose them or have someone steal them.
CloudHSM is hardware appliance based for key management and crypto operations.
AWS doesn't seem to support any sort of asymmetric public/private key cryptography? True? Why? Why not?
Ah, maybe you can use KMS in conjunction with asymmetrical keys. Maybe use asymmetrical keys to encrypt symmetric keys?
And using asymmetric keys with S3.
And KSM has envelope encryption. This looks sort of asymmetrical?
This person is confused and so am i.
And an opinion.
And yes, Cryptographic systems have multiple potential points of failure. E.g.
And finally a good AWS webinar.
PS
This is an online (browser) simulation of a German code machine, the Lorenz SZ40/42 cipher attachment, Try it out!
PPS
Still forgot most of this for the practice quiz, so here's a reminder of some important details from the whitepaper.
Encrypt
A basic function of AWS KMS is to encrypt an object under a CMK.
By design, AWS KMS provides low latency cryptographic operations on dedicated HSAs. A result of this is a limit of 4 KB on the amount of plaintext that can be encrypted in a direct call to the encrypt function.
Envelope encryption is used to encrypt larger messages.
AWS KMS, after authenticating the command, will acquire the current active EKT pertaining to the CMK. It will pass the EKT along with the customer provided plaintext and encryption context to any available HSA in the region over an authenticated session between the AWS KMS host and an HSA in the domain. The HSA will execute the following:
1. Decrypt the EKT to obtain the HBK = Decrypt(DKi , EKT).
2. Determine a 256-bit encryption key K from HBK.
3. Encrypt the plaintext ciphertext = Encrypt(K, context, plaintext). The ciphertext value is returned to the customer, and is not retained anywhere in the AWS infrastructure. Without possession of the ciphertext and the encryption context, and the authorization to use the CMK, the underlying plaintext cannot be returned.




Super new, please update us with latest new on AWS. If anyone want to get trained and get certified in AWS, then go through the AWS Online Course
ReplyDeleteAmazon Web Services Certification
ReplyDeleteWhereas, the U.S. Nationwide Institute of Requirements and Know-how (NIST) has developed the definition of Cloud Computing as a mannequin for enabling handy, on-demand community entry to a shared pool of configurable computing assets (e.g., networks, servers, storage, functions, and companies) that may be quickly provisioned and launched with a minimal administration effort or service supplier interplay.This is great blog. If you want to know more about this visit here AWS Cloud Certification.
ReplyDeleteWant to change your career in Selenium? Red Prism Group is one of the best training coaching for Selenium in Noida. Now start your career for Selenium Automation with Red Prism Group. Join training institute for selenium in noida.
ReplyDelete